how do i check if my files are suspicious
But you can also install the ClamXav program or check your MacBook and browser regularly as well. Then go to the link below to run.

Pin On Avast Support Number Uk 0808 169 1503
To begin the scan simply click the Choose file button to post your file.

. Get a personalized report now. Not the results you expected. This is where malware often hides.
Ad System Checkup will diagnose your PC in minutes. Collect a sample of the encrypted file and upload to ID Ransomware. Who is the publisher.
Check it with Windows itself. Choose where you want to search below. The file cant magically run itself if you treat it directly as data and you should be able to examine the contents.
To scan a single file that seems suspicious to you choose it by clicking on Browse. Look at the files digital signature. Nevertheless you can see if you are vulnerable.
Run it in Windows Sandbox. Run a malware scan. Thank you for the assistance.
Your best option is to scan the file using VirusTotal. To perform an anti-malware scan click Virus threat protection Click Quick Scan to scan your system for malware. It is reasonnable to assume if your machine is indeed compromised your usual monitoring tools ps top lsof have been replace with similar tools whose output looks.
How to check the exe file with Windows Defender. Press the Windows key on your keyboard the Windows symbol is found in the bottom-left corner of. To start scanning press Send.
So find your infected file first. This is a simple online tool that allows anyone to scan a file for malwareit will inspect the potentially problematic file with all sorts of different anti-malware products. When the Norton pop-up message comes up or just check your security history explore the Activity in your security history to find the file that shows up as the infected file or threat.
The only way to know if your server is compromised is to have somewhere a signature of your files and to compare your current files to it. Save the files not open usually by right clicking the link and choosing save target as or some such. The default view is to only show 4 columns on the Start-up tab.
What kind of suspicious text are you looking for. Lets check that file for threats. SirDeity Jun 23 2011 1.
That extra button is on your mouse for a reason. If you see a process that looks suspicious do. How to check Activity Monitor for Mac viruses.
If you are familiar enough with your website or content management systems CMSs code to review it for suspicious content you can check your database files and source code for signs of malware. To send several files for scanning place them in an archive WinZip WinRar or ARJ and upload this archive by clicking on Browse. The key is to make sure you do not access it with anything which could automatically run something for you.
Go to the CPU tab if youre not already in it. Improve start up internet speed and more. Suspicious looking file - Microsoft Community.
To start scanning press Send. Note that you wont be able to. If you find files that were recently modified when you were not using your PC this could mean that someone else was on your computer.
Search Search the Community. Well I did manage to stumble upon the Submit a file button. Nov 22 2002 Posts.
The simplest approach would be to use direct HTTP access to save the file and open it in Notepad to examine the contents. You can also head to Settings Update Security Windows Security Open Windows Security. Upload the file to VirusTotal.
To check malware on MacBook Apple started to build malware detection and file quarantine. Please provide instructions on how to find out which files ESET is suspicious of on my system. Here youll be able to see background processes and apps that are running including malware.
Then once you get them saved scan them with your usual antivirus as almost all of them have or should an option to scan a single file also usually by right clicking on it. One is to scan your PC with different anti-virus software perhaps running it from a USB thumb drive. Check the exes network activity for suspicious behavior.
What to do when suspicious behavior or suspicious files are found in your system When encountering encrypted files Collect a sample of the encrypted file and upload to ID Ransomware. I see no such interface. Click the CPU column to sort high to low and look for high CPU use.
As the malware has the role to steal your data you should stay protected all of the time and avoid any suspicious web pages and apps. Otherwise youll probably have to check for. Unfortunately the suspicious file is an attactment in an email sent to me.
If you have a suspicious file then there are two simple things you can do. If you just want to see if its changed you can first look at the time stamp and size of the file. If youre the administrator of the system perhaps you might find a tool like tripwire usefull.
Analyze suspicious files domains IPs and URLs to detect malware and other breaches automatically share them with the security community. Keep in mind though that those can be tricky and wont always tell you of a problem. I dont see any way to send that to Webroot.
Learn what it does. If you know the checksum of the original file you can compare it to the one you have downloaded. On Windows 10 open your Start menu type Security and click the Windows Security shortcut to open it.
Open Activity Monitor from Applications Utilities. Search the community and support articles. How to Check if a File Is Infected With a Virus.
Once the malware has been. Free Scan finds issues fast. The TEMP folder is created by the computer to pull up a program or website more easily.
But it usually contains more than just the temporary files. Take a look to all our. Marcos Eset Staff Account.
A checksum is a sequence of numbers and letters used to check data for errors. If code isnt your second language dont worry check out the next section for more information about automated malware scanning. Right -click on any of the 4 existing column headers and youll see the option to add the Command line column and others.
Windows macOS and Linux have built-in options to calculate the checksum of a file. A simple directory would suffice so I could see the file for myself. If you notice a.
TEMP Folder You can also check for spyware in the TEMP Folder. There is no Submit a file button nor any of the other options shown.

This Compromised Website Has Suspicious Javascript Code Injected In 62 Files Malware Was Found On This Website S Pages By Google Safe Malware Malicious Coding
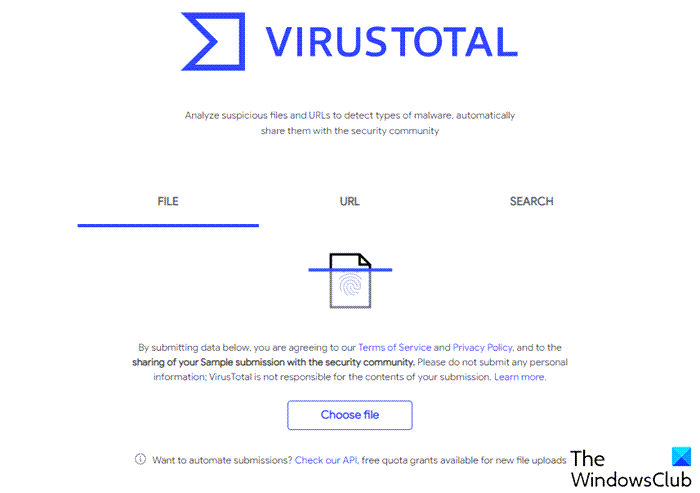
Virustotal File Scanner Url Scanner And Browser Extensions

With The Assistance Of Configserver Exploit Scanner In Short Cxs Tool You Can Perform Active Scanning Of Files Which Are U Scanner User Interface Web Based

Pin On Computing Electronic Wizardry

Generic Malware Suspicious Malwarebytes Labs Detections

Malicious Hidden Iframe Downloads Content From Suspicious Website Full Malware Analysis And Explanation Please Comment And Subsc Suspicious Malicious Content

Pin On Website Malware Monitoring

12 Most Useful Helpful Websites On The Internet You Weren T Aware Of Cool Websites Most Useful Websites New Things To Learn

Comments
Post a Comment